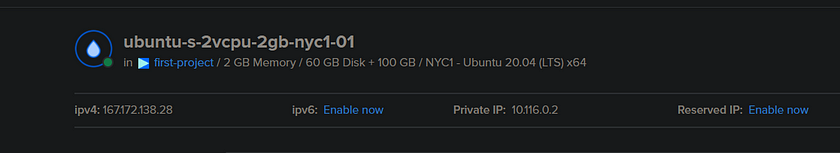
Using DigitalOcean as my CSP (Cloud Service Provider), I utilized their pooled resources via the main dashboard in order to provision a virtual machine. I’ll mention that this particular CSP aliases their vms to be called droplets; and with 2gb of virtual ram, 60gb of virtual storage, and 100gb worth of backup storage available, we are ready to begin Cloud Computing.
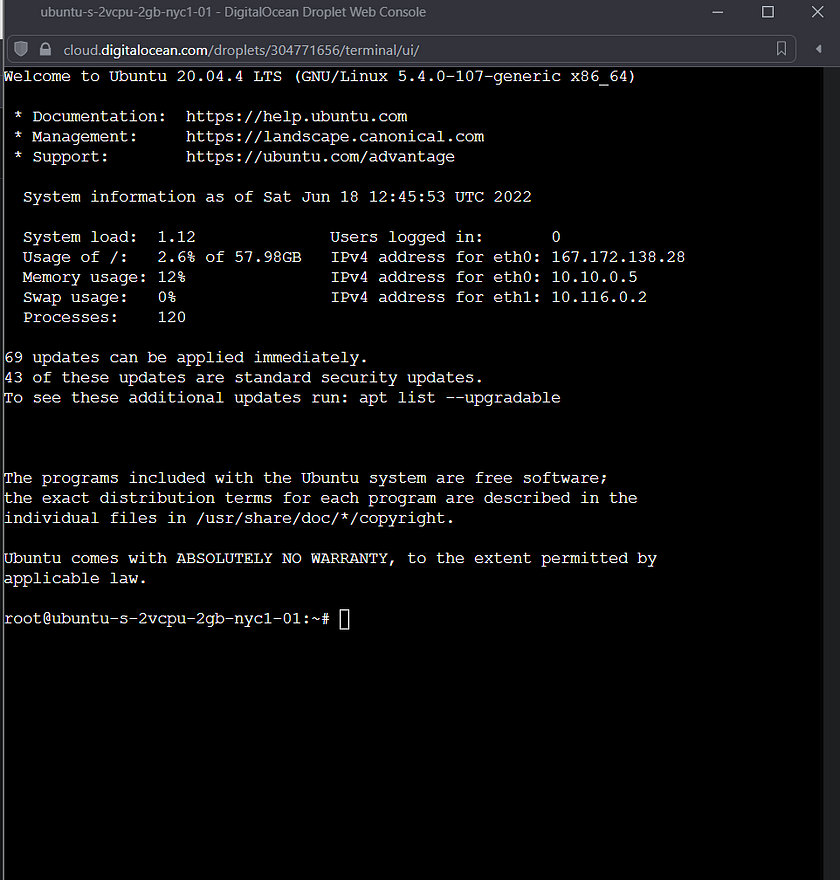
Connecting to the droplet was as easy as clicking the Console button, and within a few seconds a CLI (Command Line Interface) was at my disposal. Also note it is possible to have more than one CLI session connected at the same time.
My first thought after a successful connection is always to download and upgrade to the newest packages available for my elected Distribution, which in this case is Ubuntu20.04. Ubuntu is a Debian based distro and therefore the proper package manager would be the high level tool apt.sudo apt update && sudo apt upgrade -y
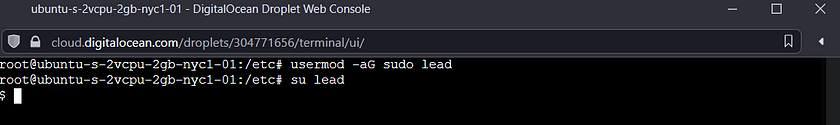
The next step I took was to follow best security practice of creating a user to manage my VM with. Using the root prompt for all commands is not recommended as it is can be easier to create problems as well as be a potential vulnerability. Therefore I created a user with the name of “lead” .
A new user does not get immediate sudo privileges, and there will be a notification displayed when the sudo command is attempted. It is possible to grant the user escalated privileges in a variety of ways such as adding the user to a sudoer group, or by editing the /etc/sudoers file directly. I chose the first method.
Next using ssh key-gen, it is possible to create public and private keys that can be used to gain trust between systems. Then it will be possible to create a secure connection.
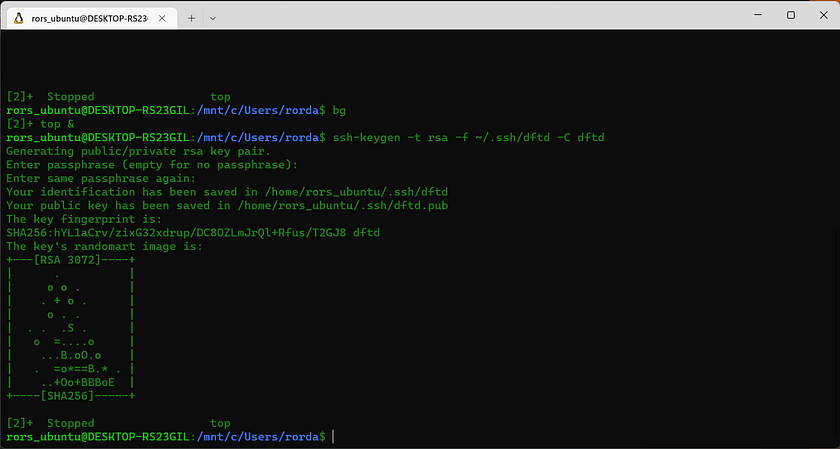
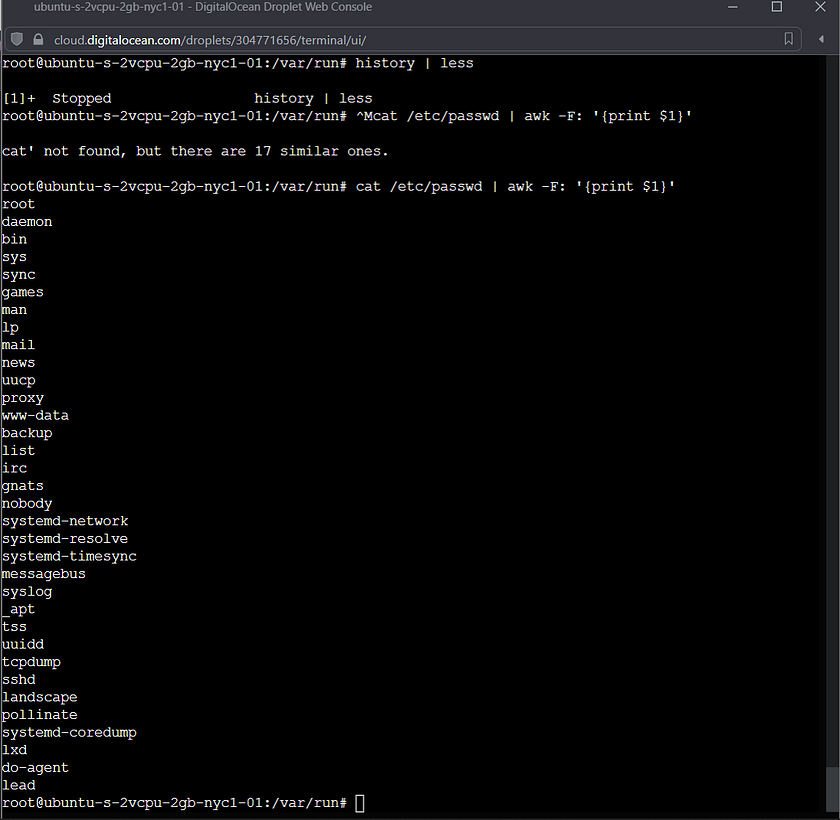
It is necessary to provide the Virtual Machine with the recently created public key. Using cat, which is short for concatenate, it is possible to display the entire key in the terminal. Then easily copy it to the computers clipboard with right click on the mouse or control c.
Back in the Virtual Machine command line, I created a file using touch and appended the text from my key using echo.
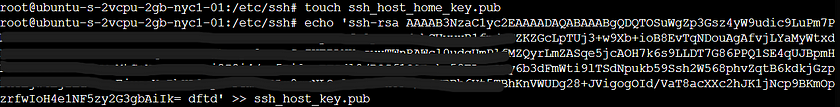
I would prefer that my computer is not compromised via ssh and therefore blocked out a few of the lines to my OS public ssh key.
Lastly in order to make a successful ssh connection, the following variables must be provided; key file location, port number, user, and public ip address.
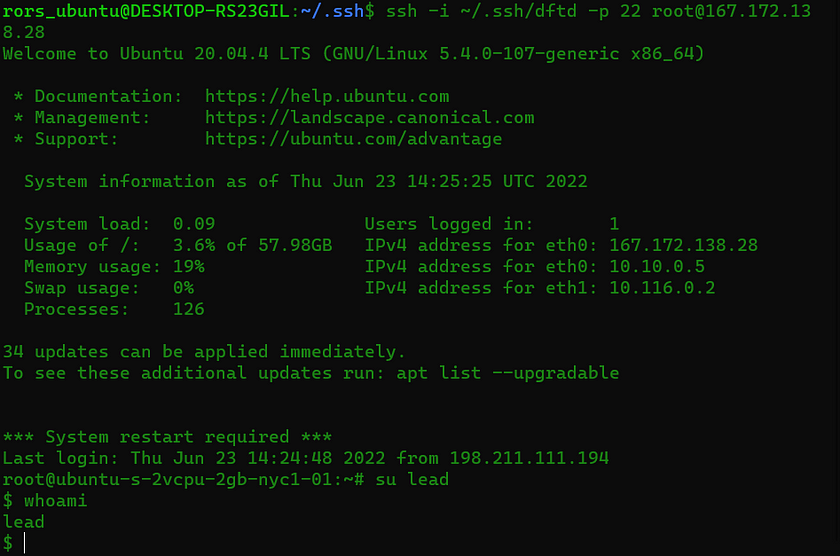
From here it is possible to have complete control over your cloud Virtual Machine via remote access. I made sure to switch over to my created user named “lead”, and then verified the switch with the command whoami.
